When Diana is the editor of the monthly Octagon Technology newsletter she likes to have a theme for the month, last month it was “Get Organised” this month her theme is the “Special Days in February” and to start things off I got Groundhog Day and the task of relating …
Get Organised – A Primer
This Back-to-Basics Primer originally started life as a theme for the Octagon Technology newsletter and evolved into a cyber security primer as it contained a range of useful articles relating to cyber security. Get Organised Month: Make a Vision Board Get Organised at Smart Thinking Solutions Organising your Files Get …
Get Organised – Business Continuity and Recovery
As the first month of 2025 draws to a close I am going to add one more article to Diana’s “Get Organised” project, this time looking briefly at business continuity. This is a companion piece to: Get Organised – Incident Response | Octagon Technology It is probably best if you …
Continue reading “Get Organised – Business Continuity and Recovery”
Ransomware never goes away
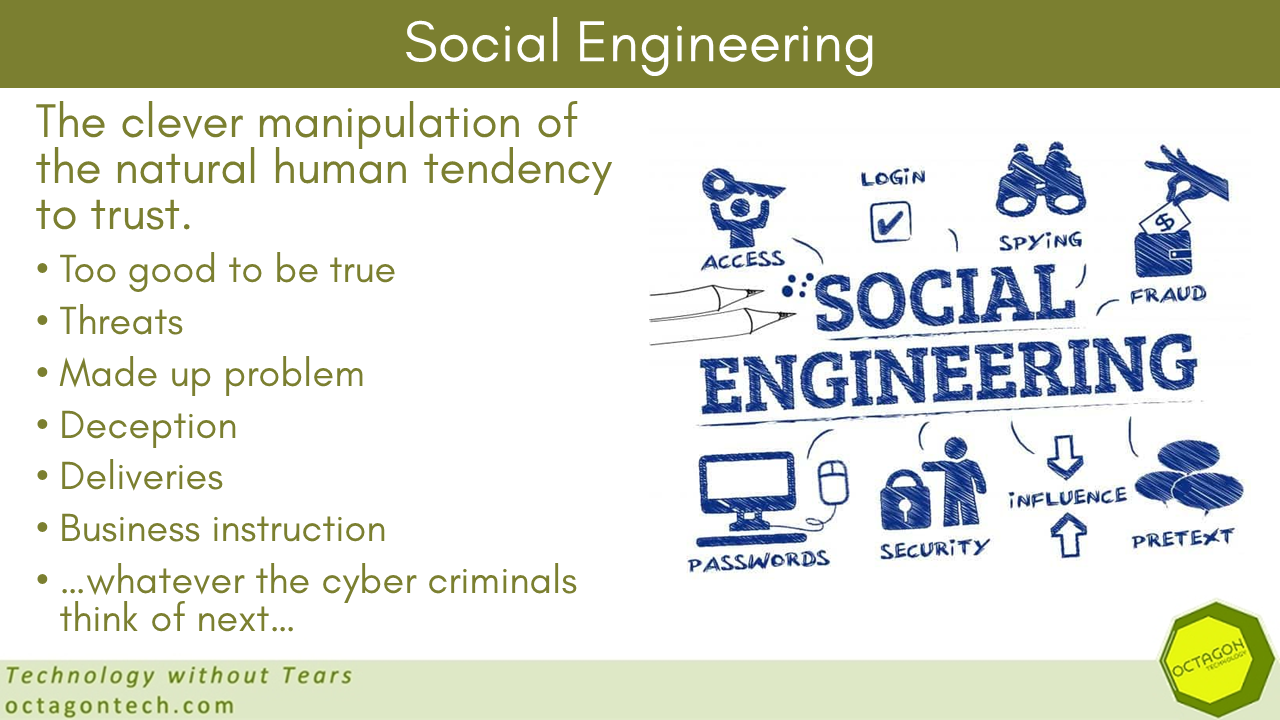
For a successful ransomware attack the threat actors have to get their malware onto a user’s computer inside the secure network. Posing as your IT support is one way to get in: Ransomware gangs pose as IT support in Microsoft Teams phishing attacks – BleepingComputer Social Engineering In this attack …
“I have a Mac – I’m secure!”
I am sure I am not alone in having heard this one from clients in the past. It was not true then and fortunately now Mac users now they are at as much risk of a cyber attack as a Windows, Linux, Android, etc. user. This malware attack uses a …