I have published part 4 of my Back-to-Basics mini-series looking at how phishing attacks work and how they impact organisations every day, over on CyberAwake. Phishing Primer – Phishing Types (pt. 4) Here are parts 1 to 3: Phishing Primer – Social Engineering (pt. 1) Phishing Primer – Social Engineering …
The Phishing Email and AI (pt. 3)
I have used the first two parts of this mini-series on Phishing attacks to look at the more general subject of social engineering because phishing is an application of social engineering aimed at you and your organisation. Start to understand the “how” of social engineering and you start to build …
Phishing Primer – Social Engineering (pt. 1)
Just because it is me, I am going to start this Back-to-Basics mini-series by not talking about phishing emails but looking at a key component of a malicious email attack – social engineering. So what is Social Engineering? In its most basic form, it is the advertising we are all …
Continue reading “Phishing Primer – Social Engineering (pt. 1)”
Something extra for the weekend.
“Beacuase It’s Friday” has been published for this week – Because It’s Friday – Electronic Mail | Smart Thinking Solutions – but as I was reading the cyber security news this morning this page came up on my BBC News feed. A BBC Newsround report from 1992 about the Michelangelo …
Social Engineering is real and costs organisations money – get your team trained.
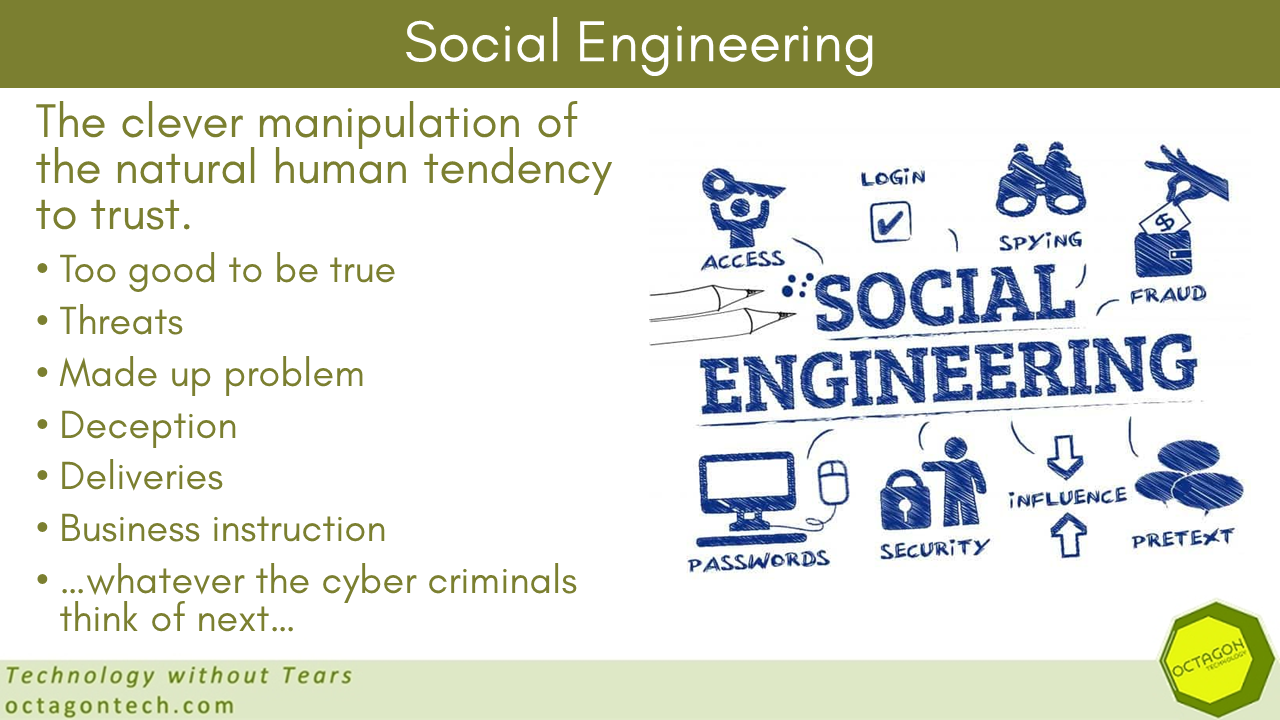
First let’s get a definition of social engineering: Social engineering is the art of manipulating people to give up confidential information. The types of information compromised can vary, but when organisations are targeted, the criminals are usually trying to trick you into giving them your credentials for secure systems you …
Continue reading “Social Engineering is real and costs organisations money – get your team trained.”