Today I am going to look at why credentials are so important in cyber security?
Credentials for identity
The management of credentials across your organisation for all services is an important impact of your cyber security, whether it is someone using the global administrator account as their “daily driver” work log-in or everyone sharing the same printer code.
Mismanagement of credentials and identity can lead to cyber security issues from a disgruntled employee stealing information using another’s login to allowing threat actors into all your information, exfiltrating it and holding you and it to ransom. So a little time spent thinking about and then implementing a proper identity management programme can save an organisation a lot of trouble.
Credentials and security
If credentials are so important why would anyone not implement every possible security step to protect them?
I often ask that question when I come into an organisation and discover they do not use multi-factor authentication or passwordless access to secure their valuable logins. Just this week when working on a cyber security review, I asked the question of an office manager, who told me they had set up MFA but it did not work and never challenged them for a OTP! He had not done anything up to that point to find out from their IT company why MFA was not working as expected! They will now I am working with them.
Remember they are the key to access your information or even to get into your building, so look after them.
Credentials for investigations
If things go wrong then you will appreciate having taken the time to correctly manage the organisation’s credentials. If the cyber security investigator can interpret the logs, look at the door entry records, watch the CCTV footage and create a story of the incident, then your organisation will be able to respond to that incident effectively and recover from it. The information gathered will also assist in mitigating other incidents in the future.
All because you can now know for certain, who did what, when and where.
But wouldn’t it be good if incidents could be anticipated?
It would but we are not magicians, well not quite!
Our expanded 24/7 continuous monitoring gathers in a raft of real-time security and operational information from you, including the logs across your Microsoft 365 environment, and applies machine learning to it, so it understands how you usually work. It then combines that with current threat analysis and sensor software to detect indicators of compromise in your systems.
If something is found two things can happen. Either the threat is escalated to the team of cyber security experts who operate the centre 24/7/365, who analyse, respond and then escalate further if required. Or in the event of a major threat the security software can take action before escalating the issue for analysis, response and support, saving vital time on those major incidents. These major threats can be defined specifically for your type of operation, but you must always include ransomware, threat actors exfiltrating your information and unsafe use of credentials etc.
Are you interested in that level of cyber security?
We launch on 1 August 2023 but you can get involved now by contacting us.
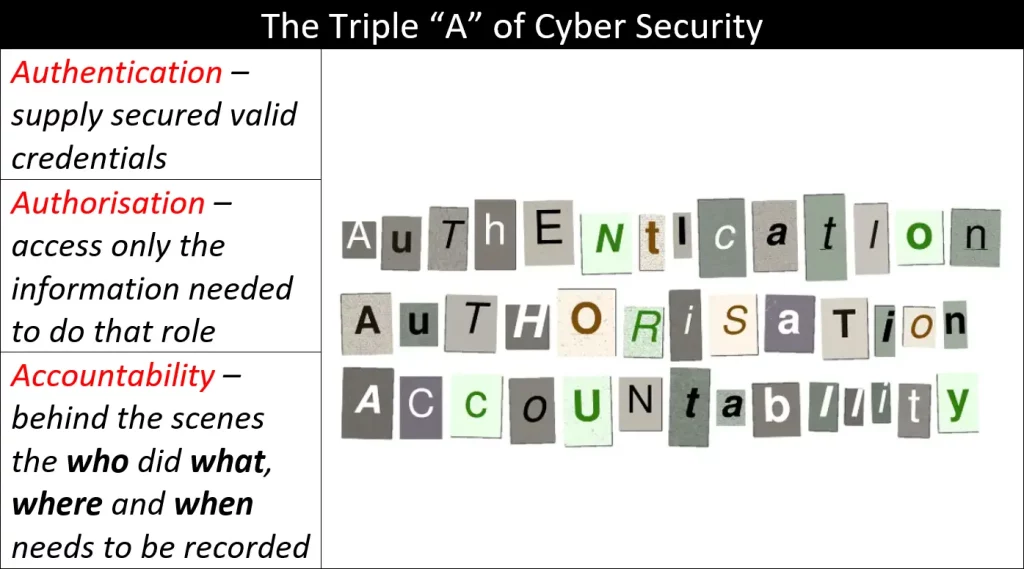
Back to Triple AAA.
This week I wrote a short series on credentials and identity by taking apart the cyber security concept of Triple A – Authentication, Authorisation and Accountability, looking at the themes I have mentioned above.
Part 1 Authentication – Who Do You Let In?
Part 2 Authorisation – It Shows You Care.
Part 3 Accountability – It Shows You are Watching.
Have a read and see how organisations need to be thinking about identity management today.
Clive Catton MSc (Cyber Security) – by-line and other articles


